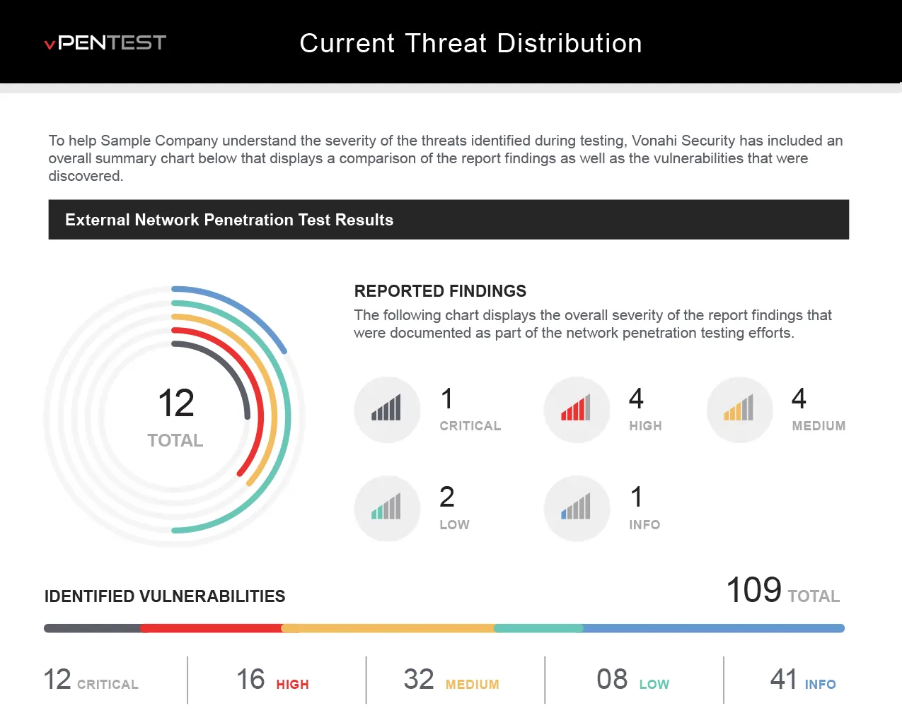
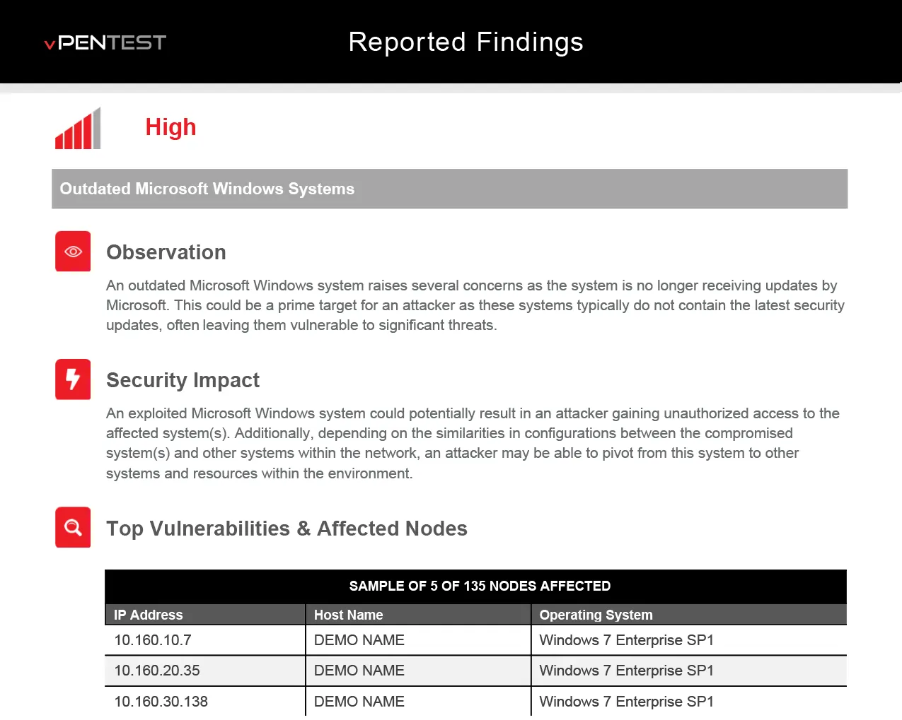
Hello World, Meet
vPENTEST
The industry’s most valued automated network penetration testing platform.
- Complete flexibility to schedule an internal or external network penetration test anytime you need it.
- More extensive and goes way beyond an automated vulnerability scan.
- Over 60% less than the cost of a traditional or manual network penetration test.
- Real-time monitoring of network penetration test and progress.
- The entire solution meets compliance requirements for regulated industries: PCI, HIPAA, SOC2, etc., and cyber insurance.
- Backed by OSCP and OSCE certified consultants with 10+ years experience.

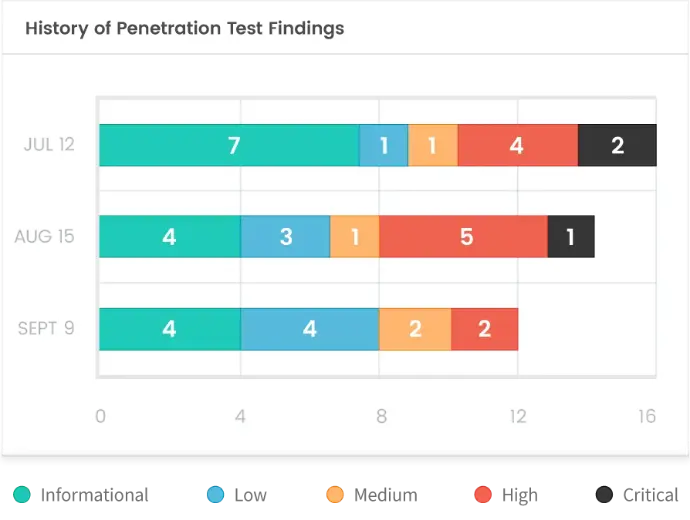
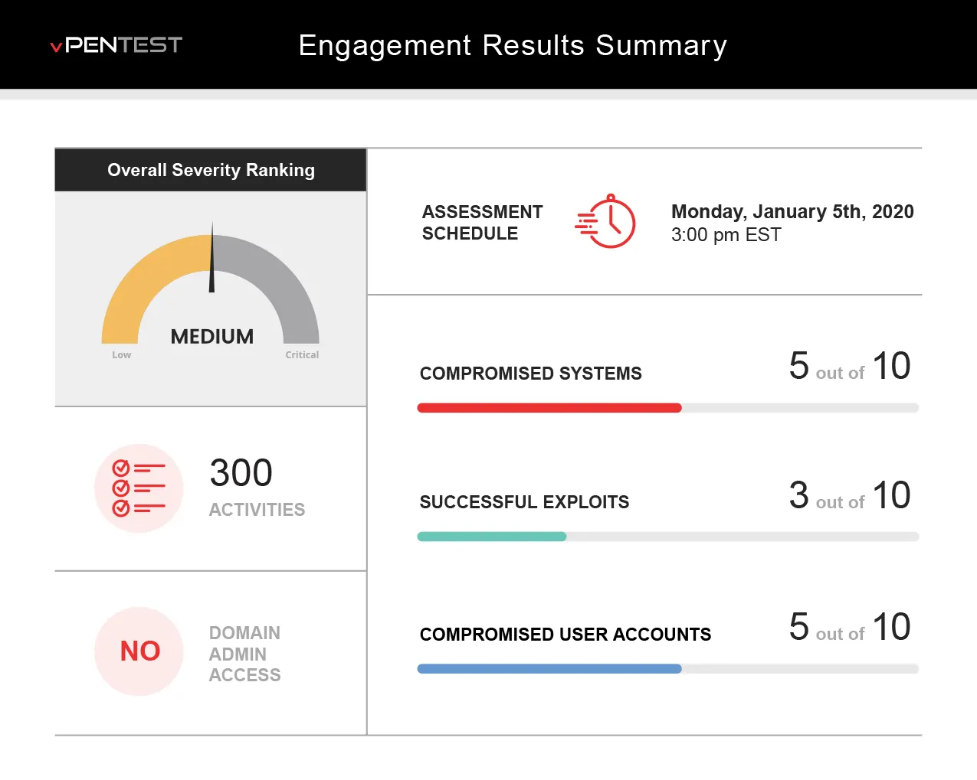
Test Your Defenses
See what a hacker sees on your network before they do.
vPenTest is essentially a hacker on a
company’s network. It looks for sensitive data, performs exploits,
conducts man-in-the-middle attacks, crack password hashes, escalates
privileges on the network, and even impersonates users to find sensitive
data. It goes beyond identifying vulnerabilities by actually exploiting
them to demonstrate what happens if an attacker got access to the
network.
Our Modern Approach to PenTesting
We make network penetration testing easy, efficient, scalable, and affordable for businesses that take cyber security seriously.
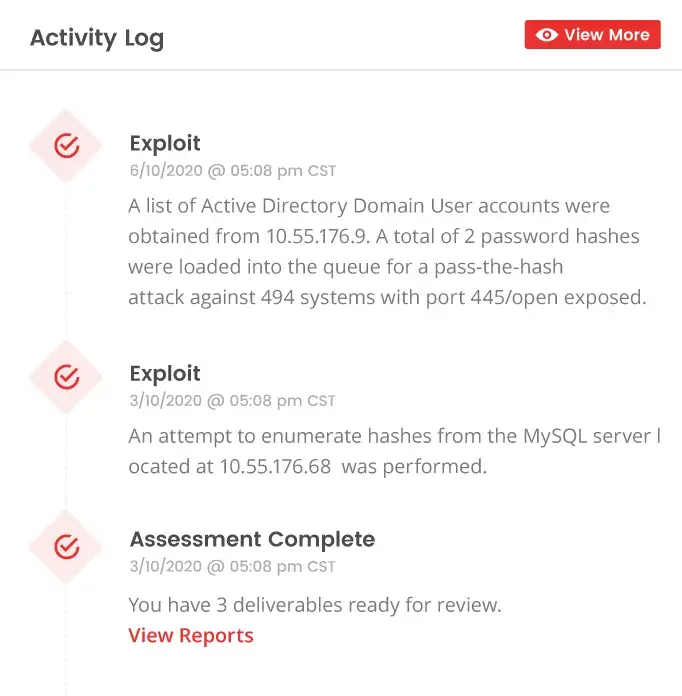
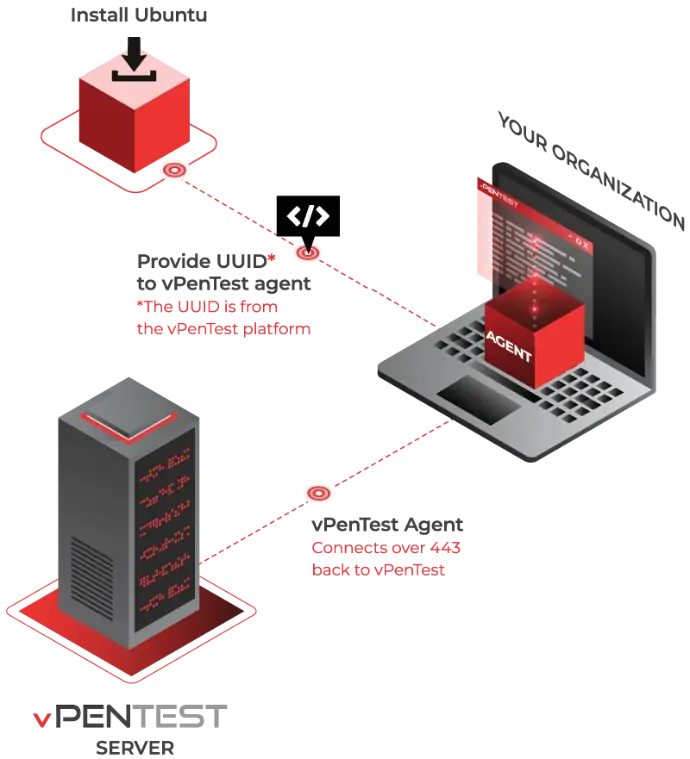
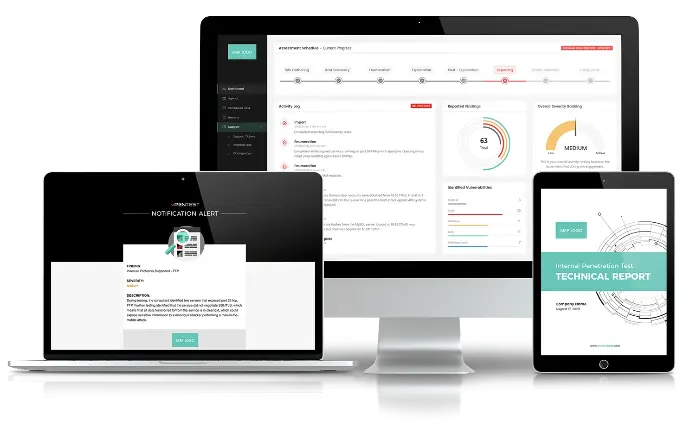
Save Time & Be in Control
Deploy an agent, schedule an internal assessment, and get detailed reports within a few days. You’re in command. You control the schedule, frequency, and scope of every assessment. Simply deploy, click and go.
Get expert penetration testing services and penetration test solutions for network penetration testing and web penetration testing. We provide cybersecurity penetration test using cloud penetration testing tool and automated penetration testing. As a trusted pen test company and penetration testing provider, we deliver top Vulnerability assessment services.
Get expert penetration testing services and penetration test solutions for network penetration testing and web penetration testing. We provide cybersecurity penetration test using cloud penetration testing tool and automated penetration testing. As a trusted pen test company and penetration testing provider, we deliver top Vulnerability assessment services.

Monitoring & RMM Tools
The Monitoring and RMM Tools by N-able empower businesses with real-time insights and control, enabling efficient oversight of IT infrastructure and facilitating proactive responses to potential issues.

Data Protection
N-able's Data Protection solutions offer robust and comprehensive measures to safeguard critical data, ensuring businesses maintain resilience against potential threats and data loss.

Cybersecurity
N-able's cybersecurity offerings deliver cutting-edge solutions, safeguarding businesses against evolving cyber threats. With advanced tools and protocols, they provide a robust defense to protect sensitive data and ensure the resilience of IT infrastructure in the face of modern security challenges.